Obtaining Direct Access To Server
his document aims at advanced users and covers the following topics:
Accessing Your SSH Account (Shell Access)
SSH Telnet is a secure form of Telnet, using an RSA key. It is a more powerful means of access than FTP in that it allows running scripts, etc. As such, SSH allows more possibilities for error, and actions which may cause harm to the server. SSH access to an account is a privilege which can be revoked if user's activities appear detrimental to the health of the server.
To request shell access to the server, do the following:

Configuration Details for your SSH Client:
Protocol: SSH2
Port 22
Cipher 3DES
MAC MD5
Authentication: Password
SSH Server: Standard
Hostname: your domain name or instant access domain
To telnet, you must use an SSH program. SSH is a more secure method of using Telnet than non-SSH Telnet. If you are using a PC we recommend SecureCRT from www.vandyke.com
A stable international version is available at Datafellows http://www.datafellows.com/download-purchase/
Users looking for a free version or users outside the United States should file through the free implementations at http://www.net.lut.ac.uk/psst/
Running Your Shell Scripts With Crontab
Crontab allows you to clock and run your own Unix shell scripts automatically. It is available only in Unix-based plans and requires the knowledge of Unix shell commands.
To enable crontab jobs, do the following:
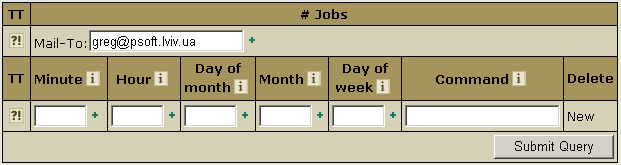
The Mail-To address is where the system will direct reports if errors occur.